In this part of the article series, we shall perform hybrid configuration. A hybrid deployment provides a unified email experience for your Office 365 deployment. It enables users who have mailboxes in their on-premises Exchange Server environment and users who have Exchange Online mailboxes to find one another in the global address list (GAL), and to send, receive, and reply to email, regardless of which system is hosting their mailbox.
Below is the list of activities performed in this article
I. Configure Hybrid between Exchange 2013 and Office 365
II. Add new DNS record to enable Office 365 to work with On-premises.
Other part of the Articles can be found at below link
Office 365 Hybrid Configuring Using Windows Azure – Part 1
Office 365 Hybrid Configuring Using Windows Azure – Part 2
Office 365 Hybrid Configuring Using Windows Azure – Part 3
Office 365 Hybrid Configuring Using Windows Azure – Part 5
Office 365 Hybrid Configuring Using Windows Azure – Part 6
Configure Hybrid between Exchange 2013 and Office 365
1. Login to the Exchange 2013 server KrisExch01.cloudapp.net
2. Before we start the hybrid configuration, we need to connect to both Exchange on-premises EAC and then connect to Office 365 console. Default Windows 2012 server Internet Explorer scripts blocks from accessing Office 365 consoles.
Given below is the fix for the same.
Internet Explore -> Internet Option -> Security -> Advance -> Add the below URL referenced in the snap.
3. Login to the Exchange EAC using Exchange organization admin account
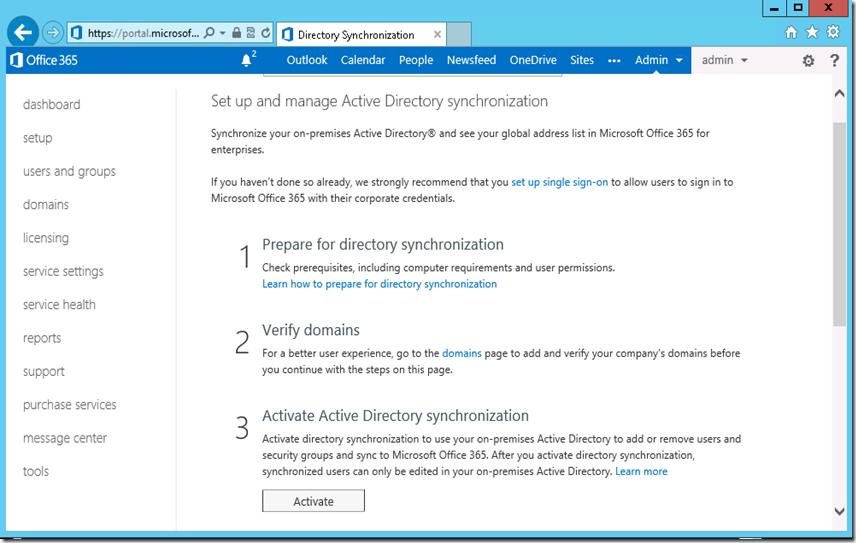
4. Click on the Hybrid -> click on ‘Enable’ to start the hybrid configuration process.
5. This will first prompt to login to Office 365, click on ‘Sign in to Office 365’
6. Login to Office 365 using the admin credentials. With this we have connected to both Office 365 and on-premises on the same console.
7. Finally, we are now ready to start the hybrid configuration. Click on ‘Enable’ again to start the Hybrid configuration wizard.
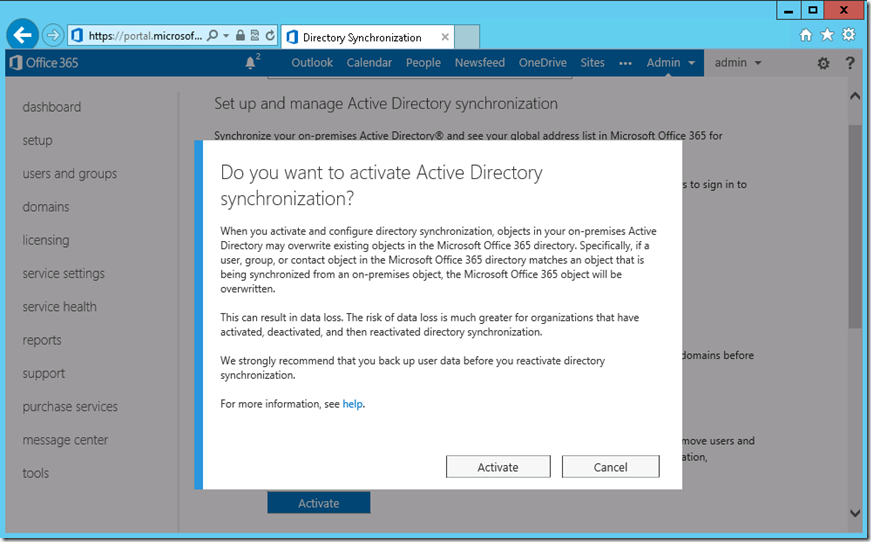
8. Select ‘Yes’ on ‘Set up Exchange Hybrid’ to confirm the hybrid configuration
9. Before we continue with the hybrid configuration, we need to re-confirm the Domain ownership. In the next page it prompts with the below statement.
“Before proceeding to the next step, copy the following tokens and create a TXT record for each token
On the public DNS to confirm domain ownership”
Login to Go Daddy for the domain checkwhatsin.com and create a TXT entry for the token. Wait for 5 minutes at the hybrid configuration wizard and click on ‘Next’ to continue
10. Below is the snapshot of the Go daddy with the TXT entry with the Token specified above
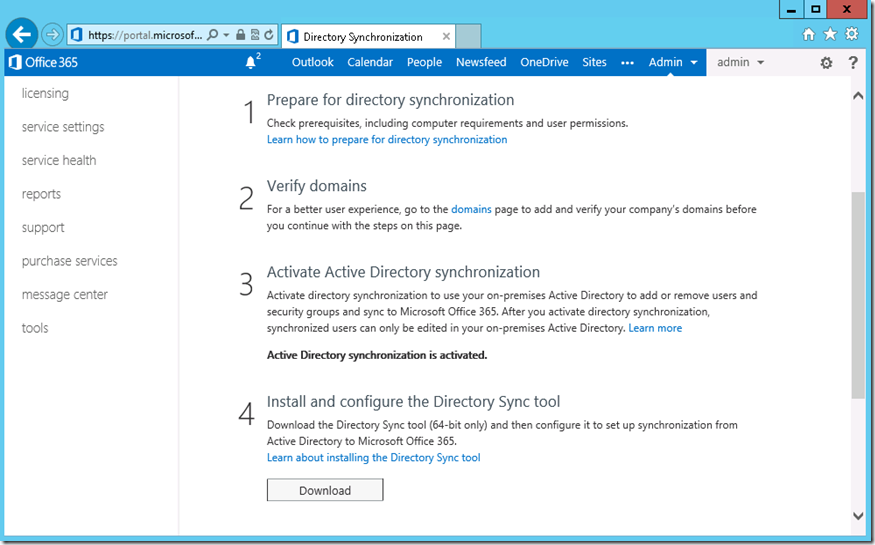
11. Since we do not have the edge transport server in our organization, select ‘Configure my Client Access and Mailbox servers for secure mail transport(typical)’ and click on ‘Next’
12. Choose one or more on-premises Client Access server to host receive connectors for secure bi-directional mail transport with Office 365. Since, we have only one Multirole server , select the server EXCH01 by using browse… button and click on ‘Next’
13. Choose one or more on-premises Mailbox server to host Send connectors for secure bi-directional mail transport with Exchange online. Since we have only one multirole server, use the ‘Browse’ button to select the server EXCH01 and click on ‘Next’ to continue
14. We need a valid certificate from trusted Certificate Authority for the secure mail transport between on-premises and Office 365. Exchange 2013 is already configured with wildcard certificate, select ‘Checkwhatsin’ certificate for the same. Click on ‘Next’ to continue
15. Enter a fully qualified domain name for the on-premises exchange server to accept email from Exchange online Protection (EOP). In our scenario we have ‘KrisExch01.cloudapp.net’ as internet facing multi-role Exchange server and the internet alias name for the same is ‘mail.checkwhatsin.com’. Specify the same and click on ‘Next’
16. Hybrid configuration needs both on-premises and Office 365 account credentials with the permission of the ‘organization management’ permission. Enter the on-premises admin credentials and click on ‘Next’ to continue
17. Enter the Office 365 admin credentials and click on ‘Next’
18. Exchange Hybrid configuration settings are now completed. Click on ‘Update’ button to configure and enable the hybrid features between Enterprise and Office 365 organization.
19. This process may take several minutes to complete. Follow the status progress bar and wait for the configuration to be completed
20. Now with this execution, the hybrid configuration has been completed successfully.
Add new DNS record to enable Office 365 to work with On-premises
In this section, we shall switch back to Office 365 continue and complete the configuration where we had left at the end of the Part 1 of this article series. We will have to complete the domain configuration by making necessary changes at ‘Chechwhatsin.com’ DNS to allow Office 365 EOP to accept all emails for checkwhatsin.com and route the email based on the mailbox location in either Office 365 or On-premises.
1. Login to Office 365 console with Org admin credentials and click on ‘domains’ -> ‘Complete setup’
2. Click on ‘Start Step 3’ to ‘Set the domain purpose and DNS configuration’.
3. On set domain purpose page, select ‘Exchange online’ and ‘I plan to set up on-premises mailboxes to work with office 365 or make sure they’re protected with Exchange online protection’ and click on ‘Next’
4. On Configure connectors page click on ‘Done, go check’. It will verify the Office 365 Outbound connectors are set up correctly to work with on-premises exchange severs.
5. Since the hybrid configuration wizard has been completed successfully, we should get the message “we’ve successfully verified that an outbound connector is setup for checkwhatsin.com”.
Now we may need to perform Autodiscover and other connectivity test using ‘Microsoft Remote connectivity Analyzer’. As we have already performed this step at part 1 of the article series, we will skip this process.
Select ‘I’ve run the tool and confirmed that my configuration is correct’ and click on ‘Next’ to continue.
6. At ‘Add DNS records’ page, it has all the necessary steps to create the manual entry at the DNS. We need to add all the DNS record specified except the autodiscover. This will allow us to keep the existing autodiscover entry point to the on-premises solution. This will help to continue the outlook configuration even after the movement of mailbox from on-premises to Office 365.
It will also add new MX record which sends all internet email for checkwhatsin.com to Office 365 Exchange online protection (EOP).
7. Below are the DNS entries at Go daddy for each of the DNS configuration specified above with the exception of Autodiscover.
8. Once the DNS entry has been added, wait for the 15 min of replication time and click on ‘Done, go check’ button for office 365 to verify the DNS entry.
We should get the successful status on all additional Office 365 records and failure status for just autodiscover entry, as we did not make the DNS entry for ‘autodiscover’ to point to address ‘autodiscover.outlook.com’.
With this we have made all the necessary changes at the Office 365 end and on-premises exchange server to work with hybrid mode.
In the next part of the article, we will be verifying and performing the final configuration at both on-premises exchange and in Office 365 in the hybrid mode.
Other part of the Articles can be found at below link
Office 365 Hybrid Configuring Using Windows Azure – Part 1
Office 365 Hybrid Configuring Using Windows Azure – Part 2
Office 365 Hybrid Configuring Using Windows Azure – Part 3