Migrating Windows Certificate Authority Server from Windows 2003 Standalone on DC to windows 2008 Enterprise Server. Dude to Various advantages on Installing CA on Windows 2008 Server like windows 2008 server supports v1, v2 and v3 certificate templates, R2 windows 2008 Enterprise CA server also supports Cross Forest Certificates. Below article helps to you migrate CA From windows 2003 Standard Edition to windows 2008 Enterprise Edition
Moving Certificate Server in Simple Steps
- Perform System State backup on Source CA Server
- Backup CA from CA Console
- Backup CA registry Configuration
- Uninstall CA from the Source Server using Add remove programs
- Install the CA as Role on the target Windows 2008 computer using existing certificate key
- Restore the CA database on the target CA
- Import the CA Registry configuration on the target CA
- Complete post-migration tasks
Perform System State backup on Source CA
- Log in to Source server and Take System State backup using Ntbackup to C:\CertBackup
Backup CA from CA Console
- Open the Certification Authority snap-in
- Right-click the node with the CA name, point to All Tasks, and then click Back Up CA.
- On the Welcome page of the CA Backup wizard, click Next. On the Items to Back Up page, select the Private key and CA certificate and Certificate database and certificate database log check boxes, enter the backup location, and then click Next
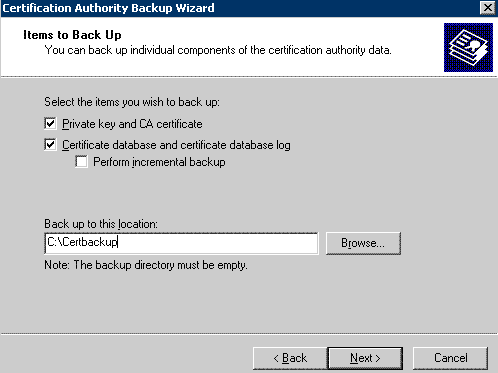
4. On the Select a Password page, enter a password to protect the CA private key and click Next.
5. On Completing the Backup Wizard page, click Finish.
6. This will create Files in C:\Certbackup
Backup CA registery Configuration
1. Click Start, point to Run, and type regedit to open the Registry Editor.
2. In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc, right-click Configuration, and then click Export.
3. Enter a location and file name, and then click Save. This creates a .reg file with the registry configuration information for your CA.
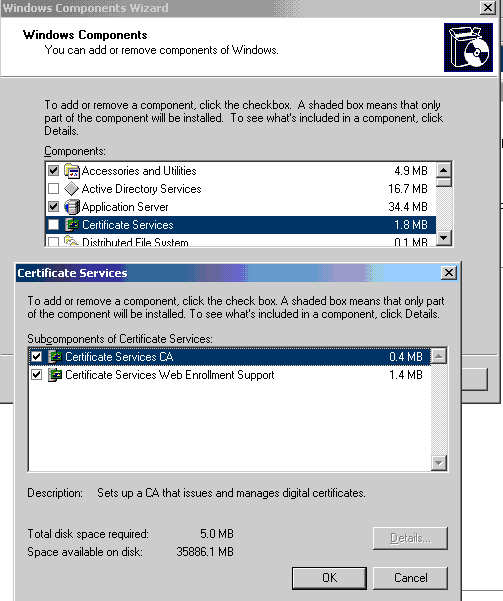
UnInstall CA from the Server using Add remove programs
1. Go To Add remove programs -> Add remove Windows components -> click on Certificate Services and uncheck on Certificate Services CA and Certificate Services Web Enrollment Support
Install the CA as Role on the target computer using exisintg certificate key
- Install New Widows 2008 Enterprise Edition Sever
- Open Server Manager and Add New Role
- Select Active Directory Certificate Services
- Select Certificate Authority and Next
- Select Enterprise CA and Next
- Use Existing Private Key as show below and select selct a certificate and user its associated private key and Next
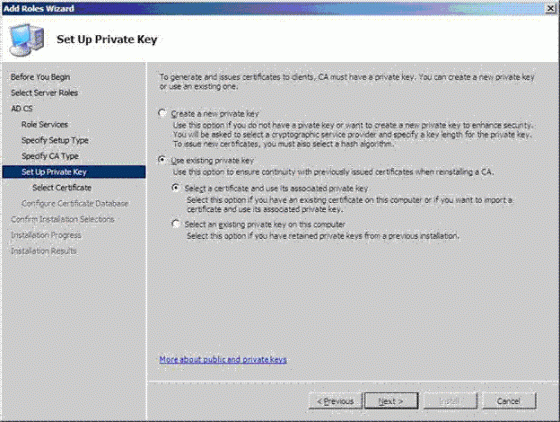
7. Click on Browse buttong to Search folder containing certificate and private key which you exported from Source computer
8. Enter the password which was used to export
9. Next , Next and click on Install
Restore the CA database on the target CA
- Open the Certification Authority snap-in.
- Right-click the node with the CA name, point to All Tasks, and then click Restore CA. Click OK to confirm stopping the CA service.
- In the CA Restore wizard, on the Welcome page, click Next.
- On the Items to Restore page, select Certificate database and certificate database log. Click Browse, and navigate to the location of the Database folder that contains the CA database export files created when you previously exported the CA database.
- Enter the password you used to export the CA database from the source CA, if a password is requested.
- Click Finish, and then click Yes to confirm restarting the CA.
Import the CA Registery configuration on the target CA.
- Double click on registery file which you exported from the source server to import the same into the server and Yes to confirm the same
Complete post-migration tasks
Updating CRL Distribution Point and Authority Information Access Extensions
- Loging to Windows 2008 New CA Server
- Open Certificate MMC
- Right click on the CA and click on Extenstion and click on ADD and add the below line by changing SourceServername.
ldap:///CN=<CATruncatedName><CRLNameSuffix>,CN=SourceServername,CN=CDP,CN=Public Key Services,CN=Services,<ConfigurationContainer><CDPObjectClass>
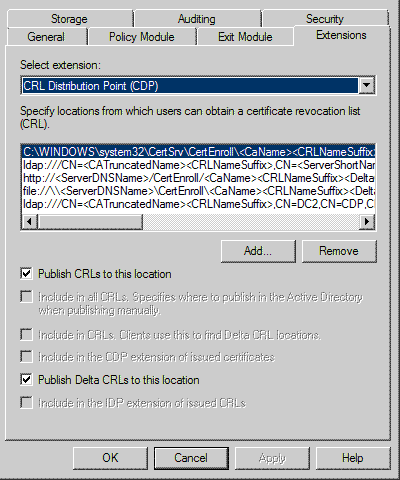
4. Check Publish CRLs to this location
5. Publish Delta CRLs to this location
6. Apply and OK
7. Verify the CA can publish CRLs to the new location.
8. Open the Certification Authority snap-in.
9. Right-click Revoked Certificates, point to All Tasks, and click Publish.
10. Click either New CRL or Delta CRL only, and click OK.
To verify ACLs on the AIA and CDP containers
- Loging to DC and open Active Direcotry Sites in Services
- On the Console click on Top Node
- Click View and Show Services node
- you will find Services folder on the Left and expand to reach Public key Services as shown below
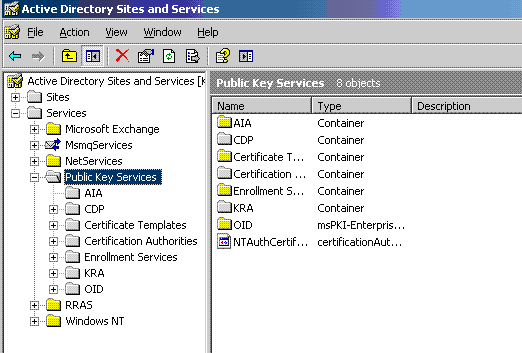
5. Expand Public Key Services
6. click AIA folder and In the details pane, select the name of the source CA.
7. On the Action menu, click Properties.
8. Click the Security tab, and then click Add.
9. Click Object Types, click Computers, and then click OK.
10. Type the host name of the target CA, and click OK.
11. In the Allow column, select Full Control, and click OK.
12. In the left pane, select CDP and the host name of the source CA.
13. In the details pane, select the first CRL object.
14. On the Action menu, click Properties, and then click the Security tab.
15. In the list of permitted group or user names, select the name of the source CA, click Remove, and then click Add.
16. Click Object Types, select Computers, and then click OK.
17. Type the host name of the target CA, and click OK.
18. In the Allow column, select Full Control, and then click OK.
19. In the details pane, select the next CRL object, and repeat steps 14 through 18 until you have reached the last object.
Verifying ReGistery
1. Verify that CAServerName is a registry string value located under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\CAName\ registry key. It should be updated to represent the DNS or the host of the new CA host.
2. Verify that CACertPublicationURLs and CRLPublicationURLs are both registry multi-string values located under the same key as CAServerName.
3. Check the remaining registry values under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc registry key, with emphasis on any values that have been customized to ensure that they are free of data containing the old CA host name or other invalid CA settings. For example:
- Configuration\ConfigurationDirectory
- Configuration\CAName\CACertFilename